andrijapanicsb opened a new issue #3602: Using custom protocol in ACL rule, breaks ACL URL: https://github.com/apache/cloudstack/issues/3602 <!-- Verify first that your issue/request is not already reported on GitHub. Also test if the latest release and master branch are affected too. Always add information AFTER of these HTML comments, but no need to delete the comments. --> ##### ISSUE TYPE <!-- Pick one below and delete the rest --> * Bug Report ##### COMPONENT NAME <!-- Categorize the issue, e.g. API, VR, VPN, UI, etc. --> ~~~ mgmt, ACL rules handling ~~~ ##### CLOUDSTACK VERSION <!-- New line separated list of affected versions, commit ID for issues on master branch. --> ~~~ tested 4.11.2.0, 4.13.0.0 ~~~ ##### CONFIGURATION <!-- Information about the configuration if relevant, e.g. basic network, advanced networking, etc. N/A otherwise --> VPC, custom ACL with a few (ingress) rules applied to a network ##### OS / ENVIRONMENT <!-- Information about the environment if relevant, N/A otherwise --> NA ##### SUMMARY <!-- Explain the problem/feature briefly --> Adding an ACL rule with a custom **protocol number** (i.e. protocol 50, 51 or any other) - will break ACL/iptables chain inside the VR in following way - all the rules BEFORE this one (rule number lower than the custom protocol rule number) will get properly applied - this specific rule (custom protocol number) will NOT be injected at all inside the VR (seems it is not sent by mgmt server to the VR ) - all the rules that come AFTER this one, will be injected only AFTER the default DENY rule is injected ##### STEPS TO REPRODUCE <!-- For bugs, show exactly how to reproduce the problem, using a minimal test-case. Use Screenshots if accurate. For new features, show how the feature would be used. --> <!-- Paste example playbooks or commands between quotes below --> Create a VPC with custom ACL on the network i.e.: 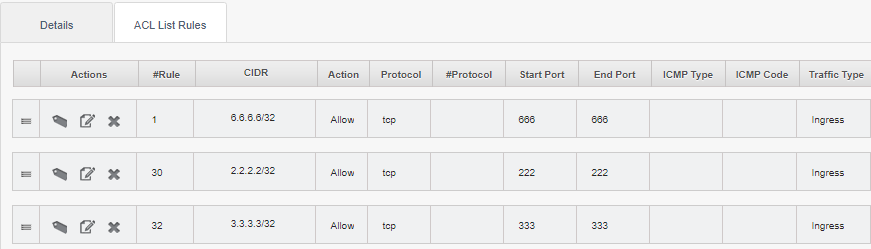 Confirm rules are properly applied inside the VR: ``` root@r-47-VM:~# iptables-save | grep INBOUND_eth2 :ACL_INBOUND_eth2 - [0:0] -A FORWARD -d 10.10.10.0/24 -o eth2 -j ACL_INBOUND_eth2 -A ACL_INBOUND_eth2 -d 225.0.0.50/32 -j ACCEPT -A ACL_INBOUND_eth2 -d 224.0.0.18/32 -j ACCEPT -A ACL_INBOUND_eth2 -s 6.6.6.6/32 -p tcp -m tcp --dport 666 -j ACCEPT -A ACL_INBOUND_eth2 -s 2.2.2.2/32 -p tcp -m tcp --dport 222 -j ACCEPT -A ACL_INBOUND_eth2 -s 3.3.3.3/32 -p tcp -m tcp --dport 333 -j ACCEPT -A ACL_INBOUND_eth2 -j DROP ``` Now, add a custom rule in the middle of the rules list (rule number 31 in the example below), as follows: 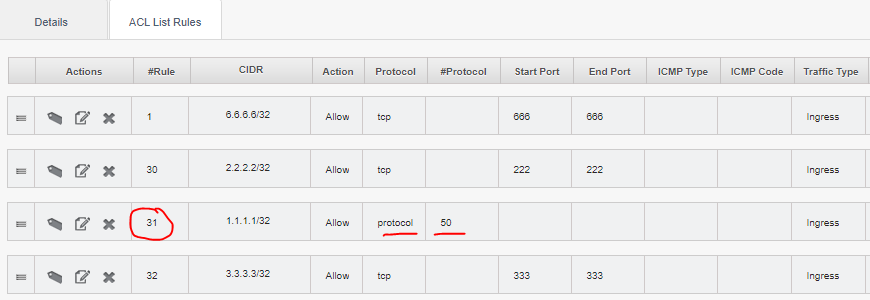 Again examine the rules in the VR: ``` root@r-47-VM:~# iptables-save | grep INBOUND_eth2 :ACL_INBOUND_eth2 - [0:0] -A FORWARD -d 10.10.10.0/24 -o eth2 -j ACL_INBOUND_eth2 -A ACL_INBOUND_eth2 -d 225.0.0.50/32 -j ACCEPT -A ACL_INBOUND_eth2 -d 224.0.0.18/32 -j ACCEPT -A ACL_INBOUND_eth2 -s 6.6.6.6/32 -p tcp -m tcp --dport 666 -j ACCEPT -A ACL_INBOUND_eth2 -s 2.2.2.2/32 -p tcp -m tcp --dport 222 -j ACCEPT -A ACL_INBOUND_eth2 -j DROP -A ACL_INBOUND_eth2 -s 3.3.3.3/32 -p tcp -m tcp --dport 333 -j ACCEPT ``` Notice that: - the rule for protocol 50 is missing (not even mentioned in the /var/log/cloud.log, while inside the management.log there is simply a "success" adding a rule - i.e. no exceptions) - the default DENY rule is applied in the middle of the chain - other rules (the ones that should come after the custom protocol number rule) are added later, below the DENY rule (so they never get evaluated) <!-- You can also paste gist.github.com links for larger files --> ##### EXPECTED RESULTS <!-- What did you expect to happen when running the steps above? --> ~~~ A working ACL. ~~~ ##### ACTUAL RESULTS <!-- What actually happened? --> <!-- Paste verbatim command output between quotes below --> ~~~ Read the "STEPS TO REPRODUCE" section. ~~~
---------------------------------------------------------------- This is an automated message from the Apache Git Service. To respond to the message, please log on to GitHub and use the URL above to go to the specific comment. For queries about this service, please contact Infrastructure at: [email protected] With regards, Apache Git Services
