[
https://issues.apache.org/jira/browse/NIFI-4199?page=com.atlassian.jira.plugin.system.issuetabpanels:comment-tabpanel&focusedCommentId=16480373#comment-16480373
]
ASF GitHub Bot commented on NIFI-4199:
--------------------------------------
Github user ijokarumawak commented on the issue:
https://github.com/apache/nifi/pull/2704
Added 3 more commits.
1. Added proxy support to Azure processors.
2. Adding more explicit Proxy spec check and doc. Due to the restrictions
of underlying libraries, Proxy support spec varies. Based on the investigation
summarized in this PR's description, I've used 4 labels to represent spec HTTP,
HTTP_AUTH, SOCKS and SOCKS_AUTH.
3. Incorporated review comments.
Example screenshots:
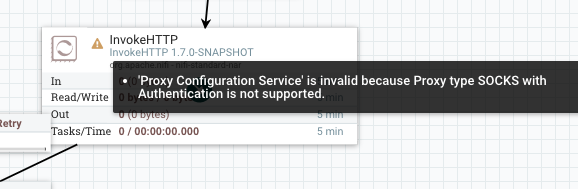
InvokeHTTP does not support SOCKS_AUTH, so if ProxyConfigurationService is
configured with SOCKS and username/password, then it becomes invalid, but SOCKS
without auth can be used:
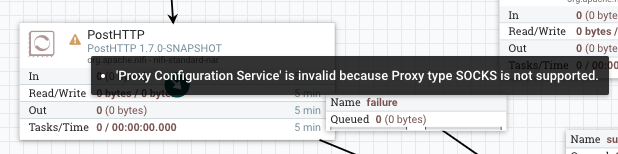
PostHTTP does not support SOCKS at all:
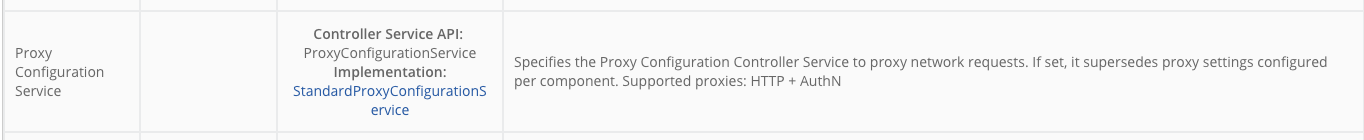
Not only validation, property description shows what proxy is supported:
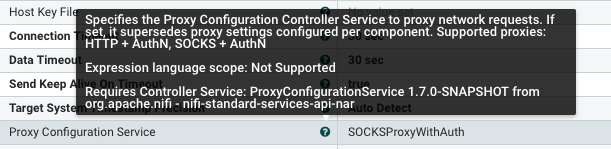
SFTP processors are the only ones supporting all Proxy specs:
> NiFi processors should be able to share proxy settings
> ------------------------------------------------------
>
> Key: NIFI-4199
> URL: https://issues.apache.org/jira/browse/NIFI-4199
> Project: Apache NiFi
> Issue Type: Improvement
> Reporter: Andre F de Miranda
> Assignee: Koji Kawamura
> Priority: Major
>
> Currently, configuring proxy settings for NiFi processors may be a tedious
> process that requires the DFM to set proxy settings on individual processors.
> This leads to:
> * Duplication of work
> * Management overhead (as password must be changed on multiple locations)
> * Lower security (as proxy credentials must be known by "n" DFMs)
> Ideally, NiFi should offer a way to minimise duplication of work by offering
> a something similar to the Standard SSL Context services. This way, the DFM
> could set the proxy settings once an all authorised users could tap into
> those settings.
--
This message was sent by Atlassian JIRA
(v7.6.3#76005)
