@NTSC-J I will fix this problem, thank you for reporting this error.
--
You are receiving this because you are subscribed to this thread.
Reply to this email directly or view it on GitHub:
https://github.com/apache/incubator-teaclave-sgx-sdk/issues/252#issuecomment-651515702
Merged #253 into master.
--
You are receiving this because you are subscribed to this thread.
Reply to this email directly or view it on GitHub:
https://github.com/apache/incubator-teaclave-sgx-sdk/pull/253#event-3495642148
`1 & ((res - 1) >> 8)`
panic: attempt to subtract with overflow
If res is 0, it will panic.
#252
You can view, comment on, or merge this pull request online at:
https://github.com/apache/incubator-teaclave-sgx-sdk/pull/253
-- Commit Summary --
* Fix consttime_memequal integer overflow bug
我们使用了 rustls [1],是 Rust rewrite 的 TLS 库,很大程度上避免了内存安全相关的漏洞,OpenSSL 的 heartbleed
漏洞 [2] 就是由内存安全问题引起的。
- [1] https://github.com/ctz/rustls
- [2] https://heartbleed.com/
--
You are receiving this because you are subscribed to this thread.
Reply to this email directly or view it on GitHub:
https://g
@mssun attested TLS用到的TLS的实现是谁提供的,实际是运行在什么环境的,会不会因为这块的实现有漏洞(比如以前open
ssl的很多漏洞)从而导致泄密?
--
You are receiving this because you are subscribed to this thread.
Reply to this email directly or view it on GitHub:
https://github.com/apache/incubator-teaclave/issues/372#issuecomment-651477482
通过 `include_str!` (https://doc.rust-lang.org/std/macro.include_str.html)。
https://github.com/apache/incubator-teaclave/blob/80fe5e9b78f3d5a023a07f9b44cabf4bd994a919/services/access_control/enclave/src/acs.rs#L33
--
You are receiving this because you are subscribed to this thread.
Reply to this e
请问下,model.conf 文件是如何编译到 enclave 中的呢?配置文件也能静态编译吗?
--
You are receiving this because you are subscribed to this thread.
Reply to this email directly or view it on GitHub:
https://github.com/apache/incubator-teaclave/issues/374#issuecomment-651473037
The main reason is that the kernel may be upgraded when you reboot the system.
You can setup your Linux distro to manually upgrade kernel.
--
You are receiving this because you are subscribed to this thread.
Reply to this email directly or view it on GitHub:
https://github.com/apache/incubator-t
> sudo systemctl restart aesmd
it work. thanks
but next time when i reboot the system.
i have to continue to reload SGX_ Driver and restart aesmd?
--
You are receiving this because you are subscribed to this thread.
Reply to this email directly or view it on GitHub:
https://github.com/apache/i
Also, try to restart the AESM daemon which helps to manage architectural
enclaves : `sudo systemctl restart aesmd`.
--
You are receiving this because you are subscribed to this thread.
Reply to this email directly or view it on GitHub:
https://github.com/apache/incubator-teaclave/issues/373#issu
> There is something wrong with your SGX environment. Please check if the SGX
> device (`/dev/isgx`) still exists.
>
> Also, I'll come up a fix to provide more information on the error.
The SGX environment and teaclave of the server were running normally. Later,
after the server was shut down a
`acs_engine.py` 和 `model.conf` 都是静态编译进 enclave 里的。
--
You are receiving this because you are subscribed to this thread.
Reply to this email directly or view it on GitHub:
https://github.com/apache/incubator-teaclave/issues/374#issuecomment-651418057
There is something wrong with your SGX environment. Please check if the SGX
device (`/dev/isgx`) still exists.
Also, I'll come up a fix to provide more information on the error.
--
You are receiving this because you are subscribed to this thread.
Reply to this email directly or view it on GitHu
@qinkunbao
非常感谢解答!
听你这样说,我应该明白了.
我可能被example所"迷惑",是我自己误解了.因为我看到是放在2个用户的key都放在同一个py文件内.
真实的场景应该是
1,用户1,用户2(相当于A1,A2)各自提交自己的payload(通过SDK方式)来创建自己的task
2,最终由平台(B)来runTask.
3,A1,A2各自等待返回的结果.
这也是我的理解,也欢迎各位指正.
--
You are receiving this because you are subscribed to this thread.
Reply to this email dir
我最近也在看SGX,这是我的理解。如有不对欢迎指出来。
A <-> B
假设A是Client,B是encalve里面的代码,首先你信任client,因为这是在你本地上的,换言之这是你自己。B是Teaclave,但是你怎么需要保证Teaclave是你相信的那个版本(比如没有篡改。。),以及它跑在一个可信的环境里面(真的在encalve里面)呢?这就需要Remote
Attestation (RA),你可以查阅Intel SGX的相关文档。
但是问题还有,比如你说的key的问题。理论上应该只有A和B知道key,A是你自己的client,你不能通过网络明文传输key是
最近读Access Control模块源码时,发现几个不太理解的问题:
(1)acs.rs 中权限校验的逻辑最终调用了acs_enforce_request() 和acs_announce_fact()
函数,而这两个函数是在acs_engine.py 脚本中实现的。请问下,teaclave 服务启动后,acs_engine.py
是被编译为二进制参与到权限校验中吗?如果没有被编译,那么当 py 脚本被人为篡改(例如篡改了acs_enforce_request() 和
acs_announce_fact()的逻辑),那么权限校验岂不是失效了?
(2)model.conf
文件被加载时
docker-compose -f docker-compose-ubuntu-1804.yml up --build
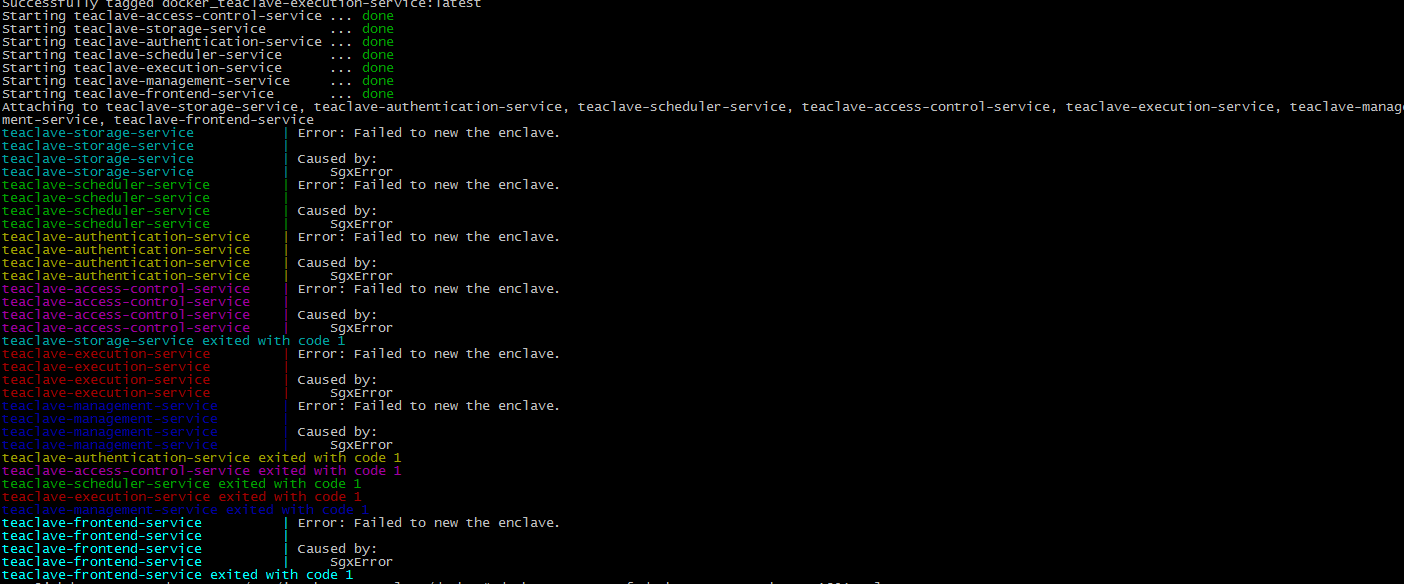
--
You are receiving this because you are subscribed to this thread.
Reply to this email directly or view it on GitHub:
htt
谢谢解答.
不过对于明文的key在脚本(builtin_private_join_and_compute.py)里还存在疑惑:
是不是只能保证这个py文件不被别人窃取,不然,别人得到这些key也是可以通过cli进行解密?
--
You are receiving this because you are subscribed to this thread.
Reply to this email directly or view it on GitHub:
https://github.com/apache/incubator-teaclave/issues/372#issuecomme
18 matches
Mail list logo
